Contents
Introduction : httpcontext.current.user.identity.name is empty windows authentication local host
When working with Windows Authentication in a local development environment, encountering an empty HttpContext.Current.User.Identity.Name can be a perplexing issue. This situation can lead to various challenges in user identification and authorization within your application. In this blog post, we will delve into the common reasons behind this behavior and explore potential solutions to ensure a seamless development experience.
HttpContext.Current.User.Identity.Name is a crucial component of ASP.NET applications, providing developers with essential information about the currently authenticated user. This property returns the name of the current user accessing the application, offering valuable insights for personalized interactions and security protocols.
Understanding Windows Authentication
Windows Authentication is a widely used mechanism to authenticate users in ASP.NET applications. It relies on the underlying Windows operating system to validate user credentials. When a user accesses a web application, their Windows identity is typically accessible through HttpContext.Current.User.Identity.Name. However, on localhost, developers may encounter situations where this value is unexpectedly empty.
The “Who are you?” question:
Windows Authentication ensures only authorized users like John can access these resources. It’s like a security guard checking your ID before letting you enter a restricted area.
The process (using a password):
- Login: John enters his username (j.doe) and password (let’s say it’s “workpassword123”).
- Behind the scenes: Windows doesn’t store passwords directly. Instead, it has a special file called the Security Accounts Manager (SAM) that holds a one-way mathematical transformation of the password, called a hash. This hash is like a unique fingerprint of the password.
- Verification: When John enters his password, Windows creates a hash of what he typed in. It then compares this hash with the one stored in the SAM file for j.doe.
- Match: If the hashes match, Windows recognizes John and grants him access.
- Mismatch: If the hashes don’t match (wrong password!), access is denied.
Additional layers of security:
Windows Authentication can also involve more secure methods beyond passwords, like:
- Smart cards: These physical cards store user credentials and require a PIN for added security.
- Biometrics: Fingerprint scanners or facial recognition can be used for authentication.
Benefits of Windows Authentication:
- Centralized management: Especially useful in company domains like Ace Inc., where user accounts and permissions can be managed centrally for all employees.
- Convenience: Users can access various resources with a single login.
Remember:
Windows Authentication is just the first step. Once John is authenticated, the system determines what resources he has permission to access based on his user account.
I hope this explanation with real-world data clarifies how Windows Authentication works!
User Experience with HttpContext.Current.User.Identity.Name
By tapping into HttpContext.Current.User.Identity.Name, developers can personalize the user experience based on individual identities. Whether it’s greeting users by their names or tailoring content to their preferences, leveraging this feature fosters a more engaging and user-centric environment.
Authentication Mode
In your web.config file, the <authentication> element should be set to use Windows authentication. This ensures that your application uses Windows authentication to identify users.
<authentication mode="Windows" />
IIS Settings
In Internet Information Services (IIS), go to your site’s authentication settings. Ensure that Windows Authentication is enabled, and other authentication methods (like Anonymous Authentication) are disabled.
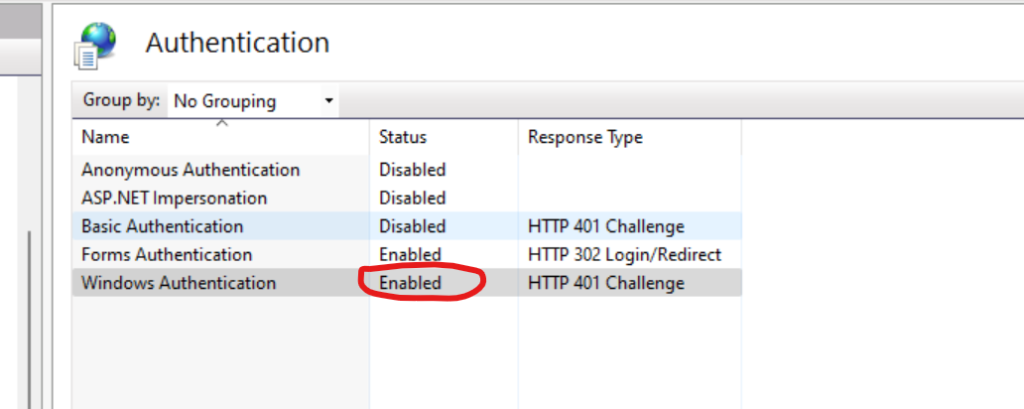
Anonymous Authentication: Anonymous Authentication should be disabled
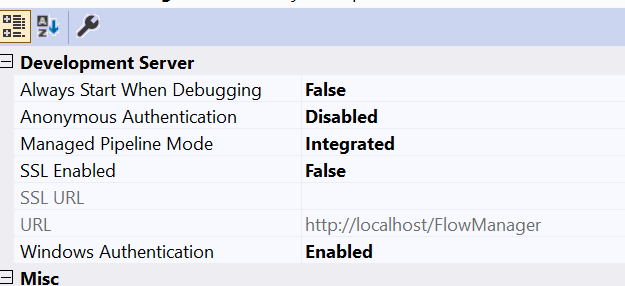
Change the project
- Select your project
- Press F4
- Disable Anonymous Authentication” and enable “Windows Authentication”
Browser Settings
Some browsers may not automatically send Windows authentication credentials, especially if they are not configured for it. Make sure your browser settings allow for Windows authentication. In Internet Explorer, for example, it should be listed in the Local Intranet zone.
Configuring Internet Explorer Settings
If you’re using Internet Explorer, follow these steps to configure Windows authentication settings:
- Open Internet Explorer and navigate to the settings menu by clicking on the gear icon located in the top-right corner of the browser window.
- From the dropdown menu, select “Internet Options.”
- In the Internet Options window, go to the “Security” tab.
- Select the “Local Intranet” zone and click on the “Custom Level” button.
- Scroll down the list of security settings until you find “Automatic logon with current user name and password.” Ensure that this setting is enabled by selecting “Automatic logon with current user name and password” and then clicking “OK” to save the changes.
- Click “OK” again to close the Internet Options window.
By configuring Internet Explorer to allow automatic logon with current user name and password in the Local Intranet zone, you ensure that Windows authentication credentials are sent automatically when accessing intranet sites or other resources within your organization’s network.
Applying Browser Settings Across Different Platforms
If you’re using a different browser or operating system, the process for enabling Windows authentication may vary. Consult the documentation or support resources provided by your browser or operating system to learn how to configure authentication settings effectively.
Testing Your Configuration
Once you’ve adjusted your browser settings, it’s essential to test the configuration to ensure that Windows authentication is functioning correctly. Access a secured resource or intranet site that requires Windows authentication and verify that you can log in seamlessly without being prompted for credentials.
Regularly Review and Update Settings
Browser settings and security configurations may evolve over time, so it’s essential to periodically review and update your settings to maintain optimal security and functionality. Stay informed about browser updates and security best practices to keep your authentication mechanisms robust and effective.
By configuring your browser settings to allow for Windows authentication, you ensure smooth and secure access to protected resources, enhancing both usability and security for users within your organization’s network.
Network Issues
Ensure that there are no network issues preventing the Windows authentication process. This includes ensuring that the client and server are on the same domain or in trusted domains.
Remember, HttpContext.Current is specific to the current request, and if you’re trying to access it outside the context of a request (for instance, in application startup or a background task), it may not be available. In such cases, consider using other means to access the current user’s identity, such as Thread.CurrentPrincipal or WindowsIdentity.GetCurrent().
By going through these details and ensuring the correct configuration at both the application and server levels, you should be able to troubleshoot and resolve issues with HttpContext.Current.User.Identity.Name being empty in the context of Windows authentication.
Best Practices for Utilizing HttpContext.Current.User.Identity.Name
Maximize the Potential of HttpContext.Current.User.Identity.Name with Best Practices
To harness the full potential of HttpContext.Current.User.Identity.Name, developers should adhere to best practices that optimize its usage:
- Ensure Proper Authentication: Always authenticate users securely before accessing HttpContext.Current.User.Identity.Name to prevent unauthorized access.
- Handle Null Values: Handle cases where HttpContext.Current.User.Identity.Name returns null gracefully to avoid potential errors.
- Implement Role-Based Access Control: Leverage user identities retrieved from HttpContext.Current.User.Identity.Name to enforce role-based access control policies efficiently.
- Secure Sensitive Information: Avoid exposing sensitive information through HttpContext.Current.User.Identity.Name, especially in error messages or logs, to prevent data breaches.
- Regularly Review Security Measures: Continuously assess and update security measures surrounding HttpContext.Current.User.Identity.Name to adapt to evolving threats and vulnerabilities.