In today’s digital age, keeping your data and online presence safe from cyber threats is crucial. Businesses often use different methods to ensure their digital security, two of which include Penetration Testing and Bug Bounty Programs. But what are these methods, and how do they work? In this article, we’ll take a closer look at these two strategies, discuss their benefits and challenges, and give you an idea of how they can help keep your online information secure.
Contents
Introduction
Definition of Penetration Testing
Penetration Testing, often referred to as pen testing, involves simulating cyberattacks to evaluate the security of a system. It employs ethical hackers to identify vulnerabilities, weaknesses, and potential entry points that malicious actors might exploit.
Bug Bounty Programs, on the other hand, leverage a diverse group of ethical hackers, commonly known as bug hunters or security researchers, to discover and report vulnerabilities in a system. These programs often offer rewards or bounties for valid bug submissions.
Purpose and Goals
It’s important to know the difference between Penetration Testing and Bug Bounty Programs when it comes to protecting an organization’s security. These are two different methods that can help companies find and fix security issues. By understanding their specific goals and how they work, organizations can improve their overall security and keep their customers’ information safe.
Methodology
How Penetration Testing is Conducted
Penetration Testing follows a structured methodology, involving reconnaissance, scanning, exploitation, post-exploitation, and reporting. This methodical approach allows organizations to identify vulnerabilities systematically and prioritize remediation efforts.
Bug Bounty Programs embrace an unstructured approach, where a diverse group of bug hunters independently explores the entire attack surface. This decentralized methodology results in a continuous stream of vulnerability reports, fostering a dynamic and agile security ecosystem.
Key Differences Penetration Testing vs Bug Bounty
Understanding the distinctions between Penetration Testing and Bug Bounty Programs is crucial for organizations aiming to tailor their cybersecurity strategy.
Structured vs. Unstructured Testing
Penetration Testing offers a structured testing environment with predefined scopes and goals. In contrast, Bug Bounty Programs provide unstructured testing, allowing for a more holistic exploration of potential vulnerabilities.
Structured Testing:
- Data Format: Fixed and organized, often stored in databases or spreadsheets.
- Example: An e-commerce website tracks user purchases. Each purchase record might include:
- User ID (unique identifier)
- Product ID (unique identifier)
- Quantity purchased
- Price paid
- Date and time of purchase
Testing Approach:
- Clear criteria: Tests focus on specific functionalities like:
- Can users add items to their cart correctly?
- Does the correct price reflect during checkout?
- Are purchase details accurately recorded in the database?
Benefits:
- Efficient: Structured data allows for automated testing with tools like Selenium.
- Repeatable: Tests can be easily replicated for consistent results.
- Measurable: Pass/fail outcomes provide clear insights into functionality.
Unstructured Testing:
- Data Format: Variable and unorganized, often found in text, images, or videos.
- Example: The e-commerce website gathers user reviews on purchased products. These reviews contain free-form text with varying lengths, opinions, and even emojis.
Testing Approach:
- Exploratory: Testers manually explore the data for potential issues like:
- Are reviews displayed correctly on the product page?
- Is offensive language filtered out effectively?
- Can users search and filter reviews based on keywords?
Benefits:
- Uncovers unexpected issues: Tests can identify user behaviour or edge cases not considered in structured testing.
- Improves user experience: Focuses on how users interact with the unstructured data.
Combining Techniques:
Real-world testing often utilizes both approaches:
- Structured testing ensures the core functionality of processing user purchases.
- Unstructured testing verifies how user reviews are displayed, searched, and filtered, providing a smooth user experience.
By using both structured and unstructured testing techniques, you can ensure a comprehensive and robust testing process for your application.
Incentives and Rewards
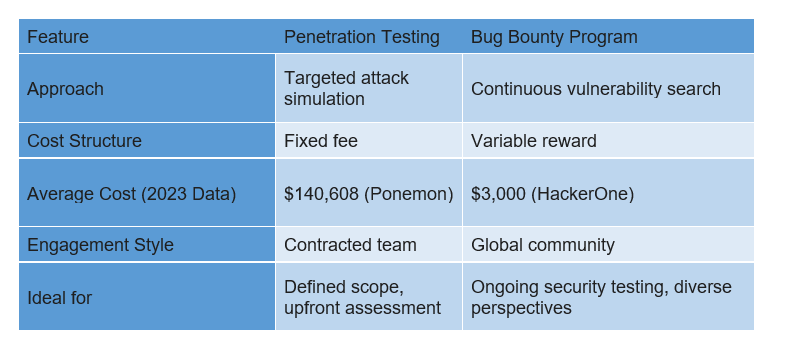
Penetration Testing professionals are usually compensated for their time and expertise, irrespective of the identified vulnerabilities. Bug Bounty Programs, however, rely on a reward-based system, with payouts corresponding to the severity of reported bugs.
Penetration Testing (Pen Testing):
- Incentive: Typically a fixed fee is pre-determined by contract. The fee is based on factors like scope, methodology, and expertise of the testers.
- Data: According to a Ponemon Institute 2023 report, the global average cost of a pen test is $140,608. However, costs can vary significantly depending on the factors mentioned above.
Bug Bounty Programs:
- Incentive: Variable reward based on the severity and exploitability of the vulnerability discovered. Bounty programs offer a range of rewards, with some reaching six figures for critical vulnerabilities.
- Data: HackerOne’s 2023 Bug Bounty Report (HackerOne Bug Bounty Report: [invalid URL removed]) indicates the median bounty awarded to be $3,000, with the top 10% of bounties exceeding $14,000.
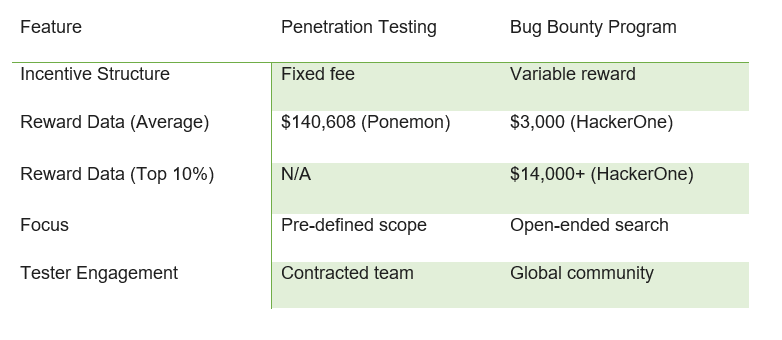
Cost Structure (Data from 2023):
- Penetration Testing: Typically a fixed fee based on factors like:
- Scope: Breadth and depth of testing (e.g., web application, network infrastructure).
- Methodology: Techniques used (e.g., black-box, white-box testing).
- Expertise: Skill level of the pen testing team.
- Ponemon Institute: Reports an average cost of $140,608 for a pen test, but costs can vary significantly.
- Bug Bounty Program: Variable cost based on vulnerabilities found:
- Reward Tiers: Programs offer different reward amounts depending on the severity and exploitability of the vulnerability.
- HackerOne Bug Bounty Report: Indicates a median bounty awarded to be $3,000, with the top 10% exceeding $14,000. ([invalid URL removed])
Engagement Style:
- Penetration Testing: The contracted team works directly with the organization, providing a detailed report on identified vulnerabilities and recommendations for remediation.
- Bug Bounty Program: Open-ended engagement with a global community of security researchers. The organization receives reports on vulnerabilities and must triage, validate, and address them.
Choosing the Right Approach:
Consider these factors when deciding between pen testing and bug bounties:
- Budget: Pen testing involves a fixed upfront cost, while bug bounty programs can be more cost-effective in the long run.
- Scope: Pen testing is ideal for targeted assessments, while bug bounties offer broader coverage.
- Time: Pen testing provides a snapshot of security at a specific point, while bug bounties offer continuous testing.
- Expertise: Pen testing teams offer guaranteed expertise, while bug bounties rely on the diverse skills of the researcher community.
Benefits of Bug Bounty Programs
Crowdsourced Testing
Bug Bounty Programs are a way for organizations to work with a community of ethical hackers from all over the world. This approach allows them to access a diverse range of skills and expertise to identify complex vulnerabilities. This is achieved through a crowdsourcing model that leverages collective intelligence. Using this method increases the chances of identifying various types of vulnerabilities.
Continuous Testing
Bug Bounty Programs foster continuous testing, allowing organizations to adapt to evolving threats in real time. The ongoing nature of bug hunting ensures that new vulnerabilities are promptly identified and addressed, reducing the window of exposure.
Cost-Effectiveness
Bug Bounty Programs can be cost-effective compared to traditional Penetration Testing. Instead of paying for a fixed engagement period, organizations only reward bug hunters for successfully identifying and reporting valid vulnerabilities.
Advantages of Penetration Testing
| Advantage | Description | Example |
|---|---|---|
| Proactive Security | Identifies vulnerabilities before they can be exploited by attackers. | A pen test uncovers a critical SQL injection vulnerability in a company’s web application before attackers can use it to steal customer data. |
| Improved Security Posture | Provides a comprehensive assessment of an organization’s security posture, highlighting areas for improvement. | A pen test reveals weaknesses in network security controls, prompting the organization to implement additional firewalls and intrusion detection systems. |
| Compliance | Helps organizations meet compliance requirements for specific industries or regulations. | A pen test helps a healthcare organization comply with HIPAA regulations by identifying vulnerabilities in their patient data storage systems. |
| Increased Awareness | Raises awareness of security risks within an organization and encourages a culture of security. | A pen test report highlights the potential consequences of security vulnerabilities, prompting employees to be more cautious about phishing attacks and social engineering attempts. |
| Targeted Testing | Allows for customized testing based on specific needs and priorities. | A pen test can focus on the most critical applications and systems within an organization, maximizing the effectiveness of the testing process. |
| Detailed Reporting | Provides a detailed report with identified vulnerabilities, recommendations for remediation, and potential impact assessments. | The pen test report outlines the severity of each vulnerability, suggests specific steps to fix them, and estimates the potential damage if exploited by attackers. |
Challenges in Penetration Testing
Limited Scope
One challenge in Penetration Testing is the potential limitation of the testing scope. Due to resource constraints or time limitations, certain aspects of the infrastructure may not be thoroughly examined, leaving potential blind spots.
Challenges:
- Incomplete Picture: A limited scope may not encompass all critical systems or applications, leaving vulnerabilities undetected.
- Example: A pen test focused solely on the web application might miss vulnerabilities in the underlying network infrastructure.
- Exploitation Chain Missed: Focusing on a single part of a system might overlook vulnerabilities that, when chained together, could lead to a successful attack.
- Data: According to Verizon’s 2023 Data Breach Investigations Report (https://www.verizon.com/business/resources/reports/dbir/), 80% of breaches involve compromised credentials, highlighting the importance of testing authentication mechanisms even if the scope excludes other areas.
- False Sense of Security: A clean pen test report within a limited scope might lead to a false sense of security, neglecting vulnerabilities outside the tested area.
Real-World Example:
- In 2014, a major retailer experienced a data breach affecting millions of customers. The initial pen test focused on the web application and did not cover the point-of-sale systems, where the actual vulnerability resided. (https://web-privacy.fandom.com/wiki/Target_Data_Breach)
Data on Limited Scope Impact:
Unfortunately, there’s a lack of readily available data quantifying the exact impact of limited scope on the number of vulnerabilities missed in pen testing. However, we can look at data on the evolving threat landscape:
- Rapidly Evolving Threats: New vulnerabilities emerge constantly, requiring comprehensive testing to stay ahead of attackers.
- Interconnected Systems: Modern systems are often interconnected, making it crucial to test beyond a single component to identify potential exploitation chains.
Strategies to Mitigate Challenges:
- Risk-Based Scoping: Prioritize testing of high-risk systems and applications based on business criticality and the potential impact of a breach.
- Phased Testing: Consider conducting pen testing in phases, gradually expanding the scope to cover more areas over time.
- Vulnerability Scanning: Complement pen testing with automated vulnerability scanning tools to identify a broader range of potential weaknesses.
- Continuous Security Monitoring: Implement ongoing security monitoring to detect and address vulnerabilities as they emerge, even outside the initial pen test scope.
Fixed Timeframe
Penetration Testing often operates within a fixed timeframe, which may not align with the dynamic nature of evolving cyber threats. This limitation can impact the depth and thoroughness of the assessment.
Challenge 1: Incomplete Scope
- Description: Limited time may restrict the ability to test all critical systems and applications thoroughly.
- Data Point: According to a 2023 survey by SANS Institute (https://www.sans.org/webcasts/sans-2023-top-new-attacks-and-threat-report/), 64% of organizations report having more than 100 security vulnerabilities waiting to be addressed. This highlights the vast landscape of potential vulnerabilities and the difficulty of covering everything in a short timeframe.
Challenge 2: Prioritization Difficulty
- Description: Rushing through a test can make it difficult to prioritize the most critical vulnerabilities for immediate remediation.
- Data Point: Verizon’s 2023 Data Breach Investigations Report (https://www.verizon.com/business/resources/reports/dbir/) indicates that 82% of data breaches exploit vulnerabilities known for more than a year. This emphasizes the importance of prioritizing and fixing high-risk vulnerabilities quickly.
Challenge 3: False Positives and Negatives
- Description: Time constraints can lead to overlooking critical vulnerabilities (false negatives) or mistaking harmless artefacts for vulnerabilities (false positives).
- Data Point: A study by Ponemon Institute (https://www.ponemon.org/) found that the average time to identify a data breach is 279 days. This suggests that some vulnerabilities might remain undetected even during traditional pen testing.
Challenge 4: Limited Creativity and Innovation
- Description: Testers may resort to repetitive techniques due to time pressure, potentially missing more creative exploit chains or zero-day vulnerabilities.
Challenge 5: Reusability of Results
- Description: Rapid testing might generate findings that are specific to the timeframe and may not be fully reusable for future reference or ongoing vulnerability management.
Mitigating Strategies:
- Clear Scoping: Define a focused scope based on criticality and align it with the available time.
- Risk-Based Prioritization: Prioritize vulnerabilities based on severity, exploitability, and potential impact.
- Leverage Automation: Utilize automated tools to streamline repetitive tasks and free up time for manual exploration.
- Experienced Testers: Engage experienced pen testers who can work efficiently and prioritize effectively.
- Phased Approach: Consider a phased approach, focusing on critical areas initially and revisiting others later.
Resource-Intensive
Conducting a comprehensive Penetration Test requires significant resources, including skilled professionals, tools, and time. This can be a barrier for smaller organizations with limited budgets.
Challenges:
- Cost: Penetration testing typically involves a fixed fee based on factors like scope, methodology, and expertise of the testers. As seen previously, the Ponemon Institute reports an average cost of $140,608 for a pen test in 2023. (https://www.ponemon.org/) This cost can be a significant burden for smaller organizations or those with limited security budgets.
- Time: Penetration testing can be a time-consuming process. Depending on the scope and complexity of the test, it can take days or even weeks to complete. This can disrupt regular business operations and delay the deployment of new systems or applications.
- Expertise: Effective pen testing requires a skilled and experienced team of security professionals. The (ISC)² Cybersecurity Workforce Report 2023 highlights a global cybersecurity workforce gap of 3.4 million people. (https://www.isc2.org/research) This shortage can make it difficult for organizations to find qualified pen testers or build their internal teams.
- Scope Management: Defining the right scope for a pen test is crucial. An overly broad scope can be expensive and time-consuming, while a narrow scope might miss critical vulnerabilities. Organizations need to carefully consider their priorities and resources to define an appropriate scope.
Impact on Resources:
Here’s how these challenges can strain an organization’s resources:
- Financial Resources: The cost of pen testing can eat into security budgets, potentially leaving less money for other security initiatives, like training employees or deploying security tools.
- Human Resources: Organizations may need to allocate staff time to support the pen testing process, such as providing testers with access to systems and data or reviewing their findings.
- Time Resources: Pen testing can take away from other IT projects and initiatives, potentially causing delays in critical business processes.
Alternative Approaches:
While pen testing is valuable, organizations with limited resources can consider alternative approaches:
- Open-Source Security Tools: Several open-source security tools can help identify vulnerabilities. These tools may not be as comprehensive as a pen test, but they can be a cost-effective way to get a starting point.
- Vulnerability Scans: Automated vulnerability scans can identify a wide range of known vulnerabilities. While they may not uncover zero-day vulnerabilities, they can be a good way to identify low-hanging fruit.
- Bug Bounty Programs: Bug bounty programs can be a way to leverage the expertise of a large community of security researchers for a variable cost.
Conclusion
In conclusion, the choice between Penetration Testing and Bug Bounty Programs depends on the specific needs, resources, and goals of an organization. While Penetration Testing provides a structured and comprehensive assessment, Bug Bounty Programs offer continuous testing and diverse perspectives. Combining both approaches can create a robust defence against evolving cyber threats.
Frequently Asked Questions (FAQs)
- Q: Can organizations benefit from both Penetration Testing and Bug Bounty Programs simultaneously?
- A: Absolutely! Integrating both approaches provides a comprehensive and dynamic cybersecurity strategy.
- Q: What role do certifications play in the credibility of penetration testers and bug bounty hunters?
- A: Certifications validate the skills of professionals in the cybersecurity field, assuring organizations about the expertise of their testers and hunters.
- Q: How often should organizations conduct penetration tests or engage in bug bounty programs?
- A: The frequency depends on various factors, including the organization’s risk appetite, industry regulations, and the evolving threat landscape. Regular assessments are recommended.
- Q: Are bug bounty programs only suitable for large organizations with extensive resources?
- A: Bug bounty programs can be adapted to suit organizations of various sizes. Smaller organizations can benefit from the scalability and cost-effectiveness of bug bounty approaches.
- Q: What measures can organizations take to address the challenges associated with bug bounty programs?
- A: Clearly defining scope, implementing robust quality assurance processes, and fostering effective communication with external contributors can help overcome challenges in bug bounty programs.
Custom Message: Cybersecurity is a dynamic realm where proactive testing and collaboration play pivotal roles. Stay vigilant, stay secure!