Code Reviews : Ultimate guide to identifying bugs and defects during code reviews
Identifying bugs and defects during code reviews is a critical aspect of ensuring the reliability and functionality of software. This process involves a thorough examination of the codebase to uncover issues that could lead to errors, malfunctions, or unexpected behavior in the application. Let’s delve into the various aspects of identifying bugs and defects during code reviews
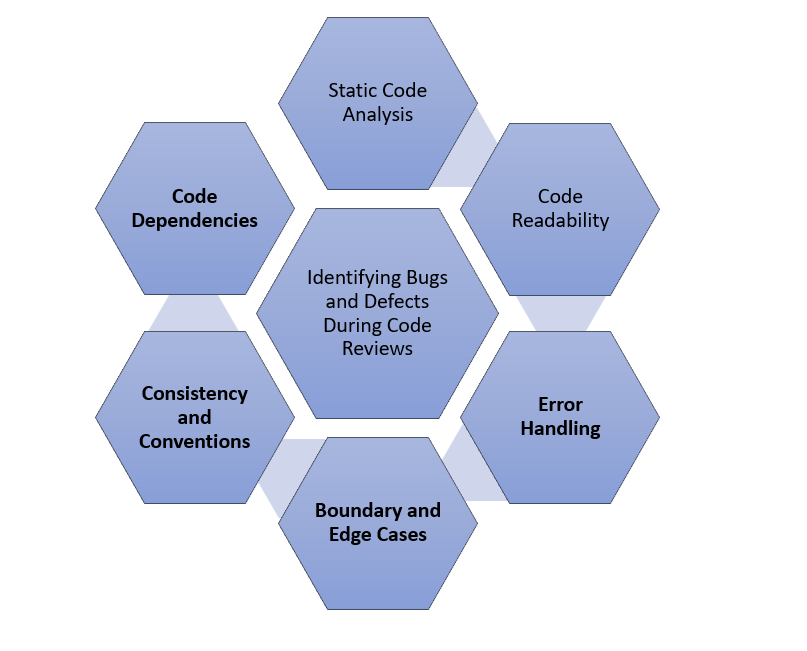
Table of Contents
Identifying Bugs and Defects During Code Reviews
1. Static Code Analysis
Static code analysis involves examining the source code without executing it. Automated tools, often integrated into the development environment or CI/CD pipelines, scan the code for potential issues. This includes detecting syntax errors, identifying code smells, and highlighting potential security vulnerabilities.
2. Code Readability
Readable code is easier to understand, maintain, and less prone to bugs. During code reviews, developers assess the code’s readability, checking for clear variable names, proper indentation, and adherence to coding standards. Poorly readable code can lead to misunderstandings and introduce bugs.
3. Error Handling
Reviewers pay special attention to how errors and exceptions are handled in the code. Proper error handling ensures that the application can gracefully recover from unexpected situations without crashing. Insufficient error handling can lead to unhandled exceptions and unexpected behavior.
4. Boundary and Edge Cases
Identifying bugs often involves testing the code with different inputs, including boundary and edge cases. Reviewers look for scenarios where the code might behave unexpectedly, such as handling the minimum or maximum values of input parameters or dealing with corner cases that may lead to unexpected results.
5. Consistency and Conventions
Consistency in coding conventions is crucial for bug prevention. Reviewers ensure that the code follows established conventions for variable naming, coding style, and design patterns. Inconsistencies can lead to confusion and introduce bugs, especially in larger codebases.
6. Code Dependencies
Dependencies between different parts of the code can introduce bugs. Reviewers assess how well the code manages dependencies, whether it uses appropriate libraries, and if the interactions with external components are handled correctly.
7. Testing and Test Coverage
Code reviews often include an examination of the associated unit tests and their coverage. Properly tested code with comprehensive test coverage is less likely to contain bugs. Reviewers assess the quality of tests, ensuring they cover critical paths and edge cases.
8. Memory Leaks and Resource Management
In languages with manual memory management, such as C or C++, memory leaks can be a significant source of bugs. Reviewers examine how the code manages memory and other resources, ensuring that allocations and deallocations are handled correctly.
9. Concurrency and Multithreading Issues
In applications with concurrent or multithreaded processes, reviewers focus on potential race conditions, deadlocks, and other synchronization issues. These can lead to subtle bugs that are hard to detect and reproduce.
Identifying bugs and defects during code reviews is a multifaceted process that involves both automated tools and human expertise. Reviewers must possess a keen eye for detail, a deep understanding of the application’s requirements, and a knowledge of best practices. By systematically examining the code for potential issues and addressing them early in the development process, teams can significantly enhance the overall quality and reliability of their software. This proactive approach to bug identification ultimately contributes to the delivery of robust and resilient software products.
Bugs and defects can manifest in various forms, ranging from minor inconveniences to critical issues that can lead to system failures. Let’s explore a few examples of common bugs and defects then you can determine how important to Identifying Bugs and Defects During Code Reviews
- Description: A null pointer exception occurs when a program attempts to access or manipulate an object or variable that is set to
null. - Example: In Java, the following code would result in a null exception
String text = null; int length = text.length(); // Throws NullPointerException
Logic Errors
- Description: Logic errors occur when the program does not behave as intended due to flawed logic in the code.
- Example: In a banking application, a logic error might lead to incorrect interest calculations, resulting in customers receiving inaccurate account statements.
Infinite Loop
- Description: An infinite loop occurs when a loop condition is never met, causing the loop to run indefinitely.
- Example: In Python, the following code creates an infinite loop
while True:
print("This is an infinite loop")Off-by-One Errors
- Description: Off-by-one errors occur when an index or counter is incremented or decremented incorrectly by one, leading to unexpected behavior.
- Example: In C, this code has an off-by-one error
int array[5];
for (int i = 0; i <= 5; i++) {
array[i] = i; // Accesses index 5, which is out of bounds
}Memory Leaks
- Description: Memory leaks occur when a program allocates memory but fails to release it, leading to a gradual depletion of available memory.
- Example: In languages like C or C++, failing to free allocated memory can result in a memory leak
int* data = malloc(sizeof(int)); // Missing free(data) leads to a memory leak
Input Validation Issues
- Description: Input validation bugs occur when the program fails to properly validate user input, potentially allowing malicious input or unintended behavior.
- Example: In a web application, inadequate input validation might allow SQL injection attacks if user input is not sanitized before being used in database queries.
Race Conditions
- Description: Race conditions occur in concurrent programming when the behavior of a program depends on the timing or sequence of events.
- Example: In a multithreaded application, a race condition might occur if two threads concurrently attempt to update a shared variable without proper synchronization.
Security Vulnerabilities
- Description: Security vulnerabilities can take various forms, including issues like cross-site scripting (XSS), cross-site request forgery (CSRF), and inadequate authentication.
- Example: In a web application, a cross-site scripting vulnerability might allow an attacker to inject malicious scripts that get executed by other users’ browsers.
Floating-Point Precision Issues
- Description: Floating-point precision errors can occur when performing arithmetic operations with floating-point numbers, leading to unexpected results.
- Example: In Python, the following code might not produce the expected result due to floating-point precision
result = 0.1 + 0.2 # Expected: 0.3, Actual: 0.30000000000000004
Compatibility Bugs
- Description: Compatibility bugs arise when the software behaves differently across different platforms, browsers, or environments.
- Example: A web application might have compatibility issues, displaying correctly in one browser but encountering layout problems in another.
These examples illustrate the diversity of bugs and defects that can occur in software development. Identifying Bugs and Defects During Code Reviews, and adherence to best practices are essential for identifying and addressing these issues early in the development process.